The second dialogue between China and EU on cross-border data transfer, potential agreement on auto data?
According to a press release from China's CAC, China and the EU have held their second dialogue on cross-border data flow, an issue that has left companies on both sides in a state of confusion.
On July 17, local time, the second meeting of the China-EU Exchange Mechanism on Cross-Border Data Flows was held in Brussels. Wang Jingtao, Deputy Director of the Cyberspace Administration of China (CAC), and Sabine Weyand, Director-General of the European Commission’s Directorate-General for Trade, co-chaired the meeting.
The meeting reviewed the positive progress made since the establishment of the mechanism and acknowledged its important role in promoting China-EU cross-border data flows. Both sides conducted in-depth, pragmatic, and constructive exchanges on topics related to cross-border data flows and, in light of the demands of their respective business communities, reached broad consensus on further leveraging the mechanism based on the principle of mutual reciprocity and promoting rules interoperability. The two parties agreed to establish a working group to cooperate on cross-border data flows in the automotive sector.
Officials from the CAC, Ministry of Industry and Information Technology (MIIT), Ministry of Commerce, and the Mission of China to the EU, as well as relevant representatives from the European Commission’s DG TRADE, DG JUST (Justice and Consumers), and DG CONNECT (Communications Networks, Content and Technology), attended the meeting.
On August 27, 2024, China and the European Union held the first meeting of the Exchange Mechanism on Cross-Border Data Flows. The analysis to this meeting is available.
The first meeting of the China-EU Exchange Mechanism on Cross-Border Data Flows was held on August 27, 2024, via video conference.
Wang Jingtao and Sabine Weyand attended the opening ceremony and delivered remarks, officially announcing the establishment of the mechanism. The meeting featured candid, in-depth, and constructive exchanges on concrete issues faced by enterprises regarding cross-border data transfers and the regulatory frameworks governing such flows. Representatives from the CAC, Ministry of Foreign Affairs, Ministry of Commerce, MIIT, National Data Administration, and the European Commission’s DG TRADE, DG JUST, DG CONNECT, and the EU Delegation to China were present.
Despite ongoing tensions in China-EU relations over trade, the Russia-Ukraine war, and China’s export controls on rare earths, the dialogue held right before the upcoming leaders’ summit is seen as a positive signal—even if the summit itself may not yield substantive outcomes.
Cross-border data transfer has become a persistent challenge in China-EU economic relations. European companies have complained that, due to China’s strict and opaque outbound data regulations, EU-based firms operating in China are unable to transfer certain industrial data back to the EU.
From what I understand, the situation for EU companies transmitting data out of China has improved in the past two years. In efforts to attract foreign investment, China has relaxed some of its outbound data controls.
The “Provisions on Promoting and Regulating Cross-Border Data Flows,” issued by the CAC in March last year, relaxed thresholds: only outbound transfers involving large volumes of personal data require security assessments. Most European companies fall below this threshold and thus are no longer subject to approval.
In my observation, Chinese government agencies appear to be providing more guidance. Authorities in sectors such as finance and natural resources are trying to clarify what constitutes “important data,” when security assessments are required, and what cases may be exempt. In April, the People’s Bank of China and several other agencies jointly released a compliance guide for outbound data transfers in the financial sector, providing clearer standards for European financial institutions.
However, the biggest challenge remains “important data”—especially industrial and non-personal data, which the EU frequently emphasizes. Under China’s new rules, unless you are notified that the data is classified as “important,” you may treat it as not important. Yet companies are still expected to self-assess and report whether they possess important data. Many EU companies report that the standards remain too vague, and they dare not take risks. This issue has been a frequent point of contention in China-EU data dialogues, including last year’s.
In recent years, the EU has also intensified investigations into Chinese platform companies, sometimes imposing hefty fines. Several Chinese internet platforms are currently under investigation by the EU for data compliance issues. Overall, the EU remains concerned that, due to China’s National Security Law and National Intelligence Law—both of which contain government access to data provisions—EU data transferred to China may not receive the same level of protection as within the EU.
This fundamental concern over China’s legal environment for data protection casts doubt on whether it is still GDPR-compliant for Chinese companies operating in the EU to transfer personal data to China (or access EU user data remotely from China) using the Standard Contractual Clauses (SCCs), the primary legal mechanism under GDPR.
In such a scenario, for cases where EU personal data is transferred to China and processed by the Chinese recipient under the SCCs (as per EU Commission Implementing Decision 2021/914), it remains unclear what specific technical, contractual, and organizational supplementary measures Chinese firms must adopt to ensure an “essentially equivalent” level of data protection as required under EU law.
The increasingly blurred boundary between personal and non-personal data in the EU is also a source of concern. Recent opinions and guidance from the European Data Protection Board (EDPB) reflect a more nuanced and dynamic understanding of anonymization and pseudonymization. Legally, the binary distinction still holds (anonymized data is outside GDPR; pseudonymized data remains within scope), but practically, the EU is introducing risk-mitigation and contextual analysis, softening earlier rigid requirements. In many cases, it is difficult to determine whether certain data is personal or non-personal.
Compared to the first dialogue, a major breakthrough in this second meeting was the reported agreement to cooperate on cross-border data flows in the automotive sector.
According to a Chinese press release, “both sides agreed to establish a working group to cooperate on cross-border data flows in the automotive sector.” While specific details about this group and its work are unclear, the auto industry is indeed an urgent area for bilateral cooperation. European automakers like BMW and Mercedes-Benz hold large market shares in China, while Chinese EV brands like BYD are actively targeting Europe.
Cross-border data flows in the auto industry involve both personal data (e.g., driver/owner information) and non-personal data (e.g., fault logs, accident records), making it a highly complex area in need of clearer compliance guidance.
In June, eight Chinese government departments jointly issued the draft “Automotive Data Outbound Security Guidelines (2025 Edition)” for public comment, which ended on July 13.
This document provides clearer guidance for European automakers operating in China and reflects China’s efforts to address concerns in this domain. Although a comprehensive data transfer agreement between China and the EU remains unlikely in the near term, reaching sector-specific agreements in areas like automotive and finance would be a highly positive step forward, and would certainly benefit industries on both sides.
To implement the Data Security Law, the Personal Information Protection Law, the Cyber Data Security Regulation, and related laws and regulations, and to establish an efficient, secure, and convenient mechanism for cross-border automotive data flows, eight departments under the national data security coordination mechanism—MIIT, CAC, NDRC, National Data Administration, Ministry of Public Security, Ministry of Natural Resources, Ministry of Transport, and the State Administration for Market Regulation—have jointly drafted the “Automotive Data Outbound Security Guidelines (2025 Edition) (Draft for Public Comment),” which is intended to be issued as a regulatory document. Public comments were invited until July 13, 2025.
Fax: +86-10-66069561
Email: zhanghong@miit.gov.cn
Mailing address: Cybersecurity Administration Bureau, MIIT, No. 13 West Chang’an Avenue, Xicheng District, Beijing, 100084, China.
Please mark the envelope with: “Feedback on Automotive Data Outbound Security Guidelines (2025 Edition) (Draft for Public Comment).”Attachment: Automotive Data Outbound Security Guidelines (2025 Edition) (Draft for Public Comment)
I translated the full draft for comment. This process was painful, but I hope it’s useful for everyone.
hese Guidelines are established in line with relevant Chinese laws and regulations, such as the Cybersecurity Law of the People's Republic of China, Data Security Law of the People's Republic of China, Personal Information Protection Law of the People's Republic of China, and Regulations on Network Data Security Management. Their aim is to guide and regulate the cross-border transfer of automotive data by data handlers, ensuring efficiency, convenience, and security, and thereby enhancing the convenience of automotive data flows across borders.
Chapter I: General Provisions
(1) : Scope of Application
Automotive data handlers shall conduct data transfer activities in accordance with these Guidelines. The automotive data referred to here includes personal and important data generated during the design, production, sale, use, and maintenance of vehicles. Automotive data handlers cover organizations engaged in automotive data processing activities, such as vehicle manufacturers, parts and software suppliers, telecom operators, autonomous driving service providers, platform operators, dealers, repair institutions, and mobility service companies.
(2) : Data Transfer Activities
The following scenarios are considered data transfer activities when automotive data handlers provide data to destinations outside the People's Republic of China (hereinafter referred to as "overseas"):
(1) Transmitting automotive data collected and generated within China during operations to overseas locations.
(2) Allowing overseas entities, organizations, or individuals to query, retrieve, download, or export data stored within China.
(3) Processing personal data of domestic individuals or conducting other data processing activities overseas as specified in Article 3(2) of the Personal Information Protection Law of the People's Republic of China.
(3) : Data Transfer Pathways
1. Automotive data handlers providing data overseas under any of the following circumstances shall apply for a data transfer security assessment:
(1) Transferring important data overseas.
(2) Transferring personal data (excluding sensitive personal data) of over one million individuals overseas from January 1 of the current year.
(3) Transferring sensitive personal data of over ten thousand individuals overseas from January 1 of the current year.
(4) Operators of critical information infrastructure transferring personal data overseas.
(5) Other circumstances explicitly stipulated by national regulations requiring a data transfer security assessment.
2. Automotive data handlers (excluding operators of critical information infrastructure) transferring personal data overseas under any of the following circumstances may choose either to conclude a standard contract for personal data transfer with the overseas recipient or to pass a personal information protection certification:
(1) Transferring personal data (excluding sensitive personal data) of between one hundred thousand and one million individuals overseas from January 1 of the current year.
(2) Transferring sensitive personal data of less than ten thousand individuals overseas from January 1 of the current year.
3. Data handlers are exempt from applying for a data transfer security assessment, concluding a standard contract for personal data transfer, or passing a personal information protection certification under any of the following circumstances:
(1) Transmitting data collected and generated overseas to China for processing and then re-transferring it overseas without involving domestic personal or important data during processing.
(2) Transferring personal data (excluding important data) overseas for the conclusion and performance of contracts where individuals are a party, such as cross-border vehicle purchases, parcel deliveries, payments, and account registrations.
(3) Transferring employee personal data (excluding important data) overseas for cross-border human resource management in accordance with labor regulations and collective contracts.
(4) Transferring personal data (excluding important data) overseas to protect life, health, and property in emergencies.
(5) Automotive data handlers other than operators of critical information infrastructure transferring personal data (excluding sensitive personal data and important data) of less than one hundred thousand individuals overseas from January 1 of the current year.
(6) Automotive data handlers registered in free trade pilot zones transferring data outside the negative list in compliance with relevant zone requirements.
(7) Data related to security vulnerabilities reported to the Ministry of Industry and Information Technology as required by the Network Product Security Vulnerability Management Regulations for vulnerability repairs.
(8) Data on vehicle product, internet-connected vehicle platform, and related system security incidents reported to the Ministry of Industry and Information Technology and relevant industry regulators in accordance with cybersecurity and data security incident emergency plans for incident handling.
(9) Source code of OTA update packages filed with the State Administration for Market Regulation for defect elimination and recall implementation as required by the Administrative Regulations on the Recall of Defective Motor Vehicle Products.
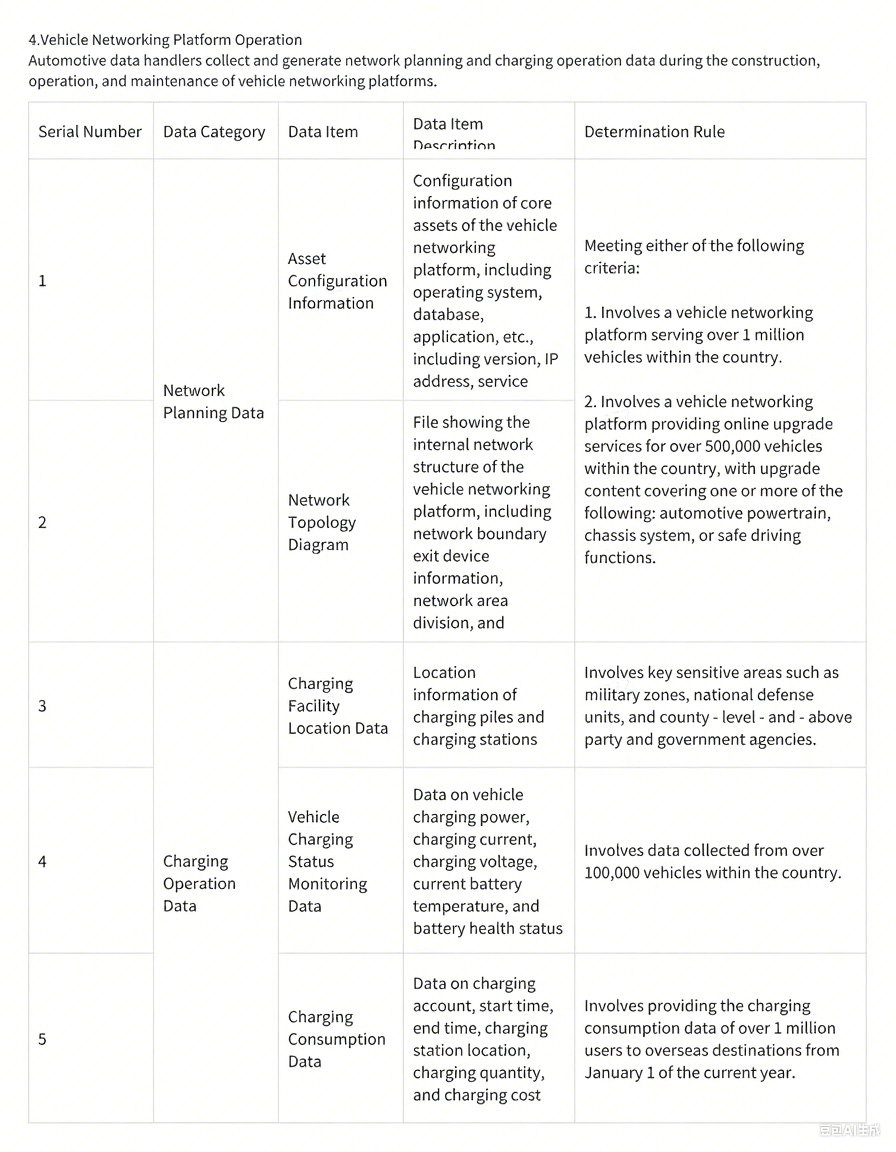
Chapter II: Important Data Transfer
Automotive data handlers providing the following important data in business scenarios shall apply for a data transfer security assessment.
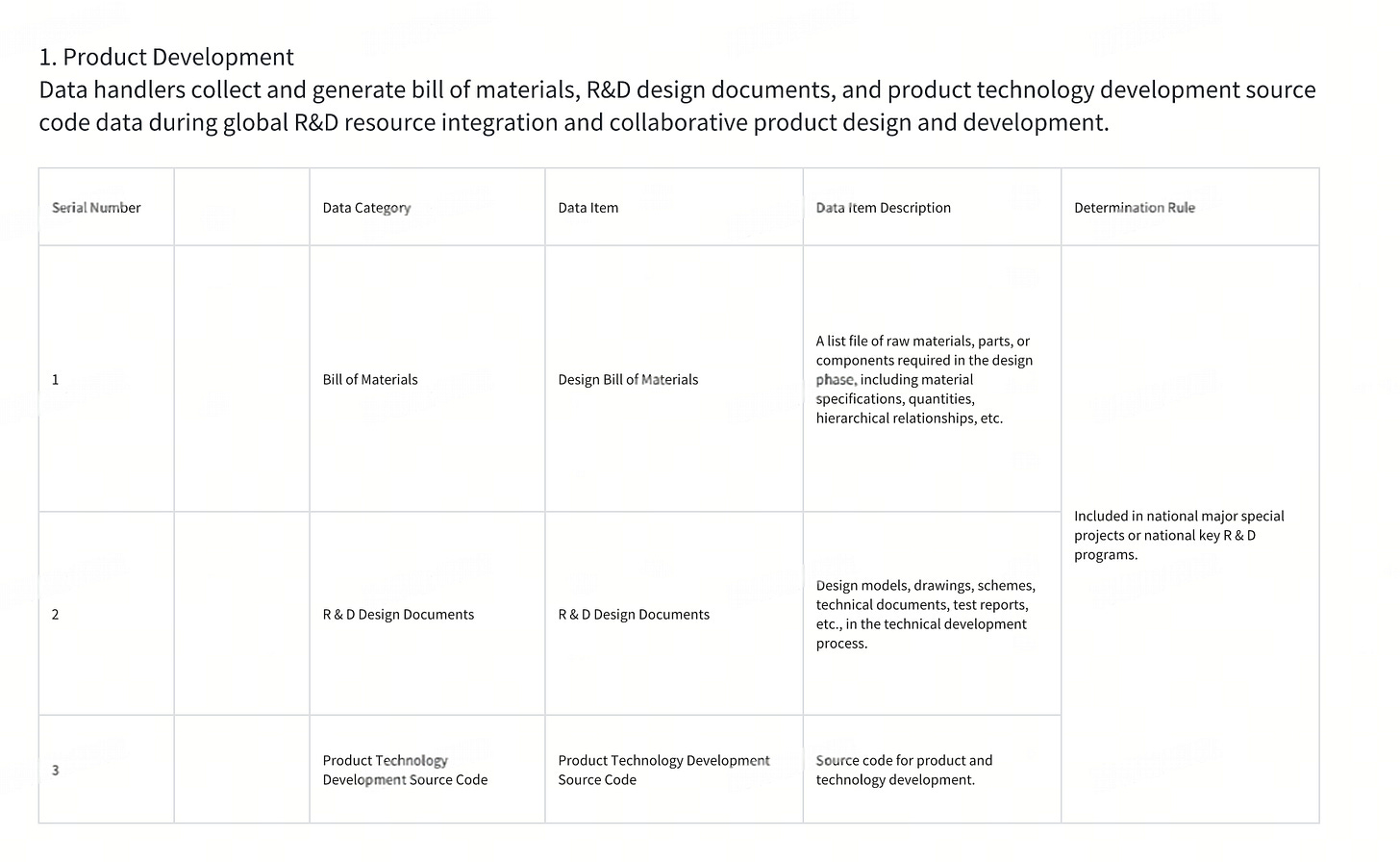
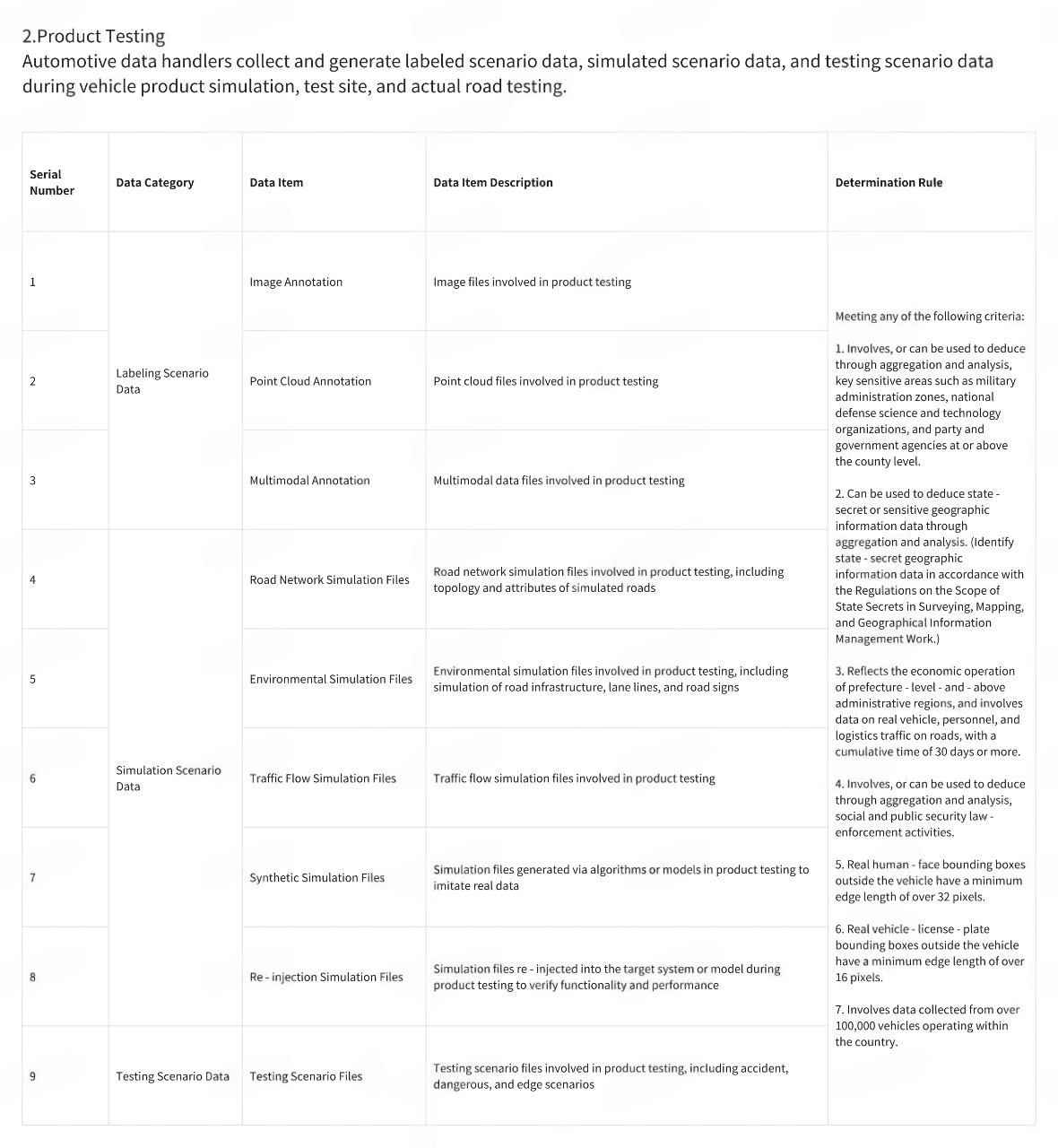
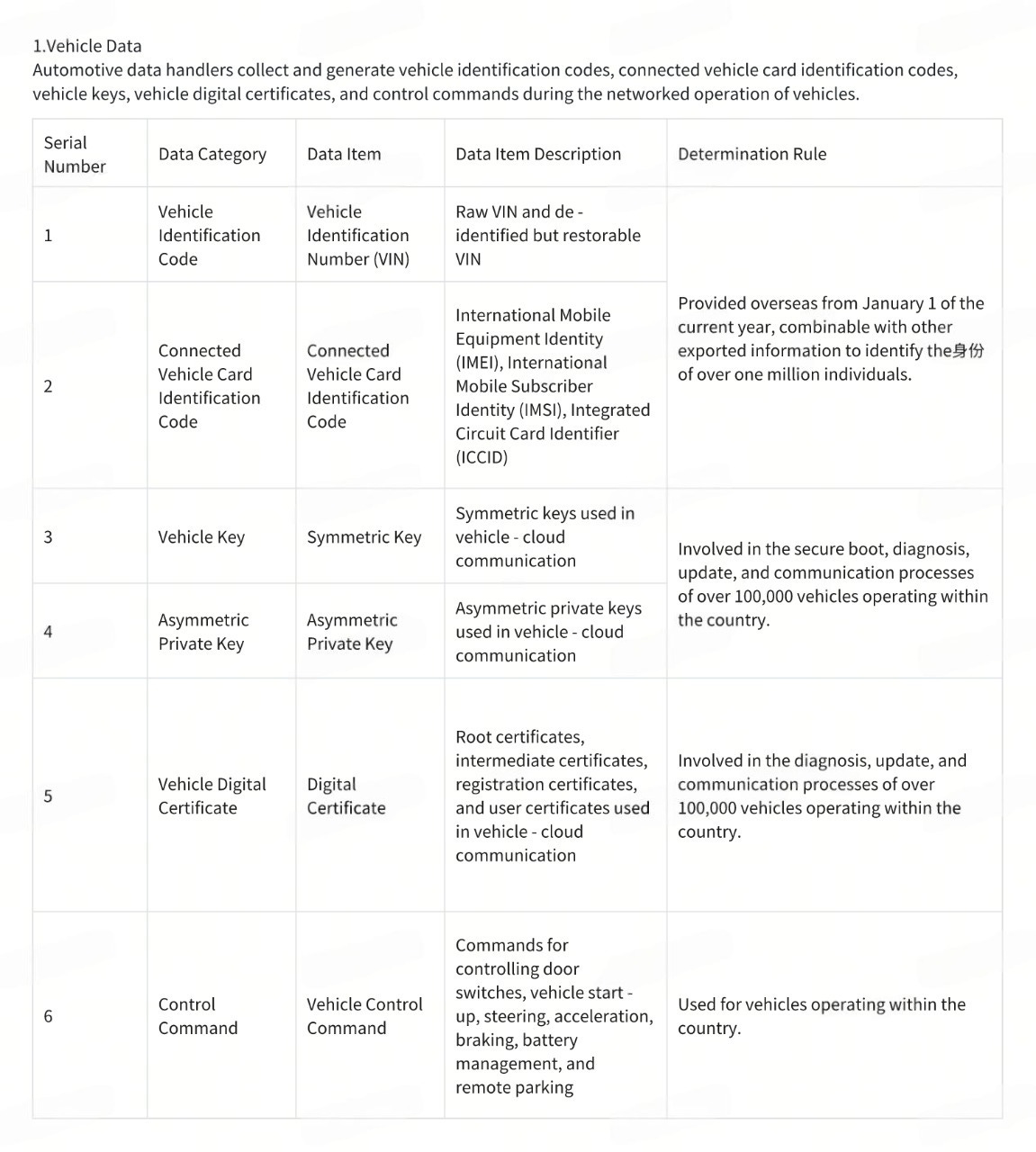
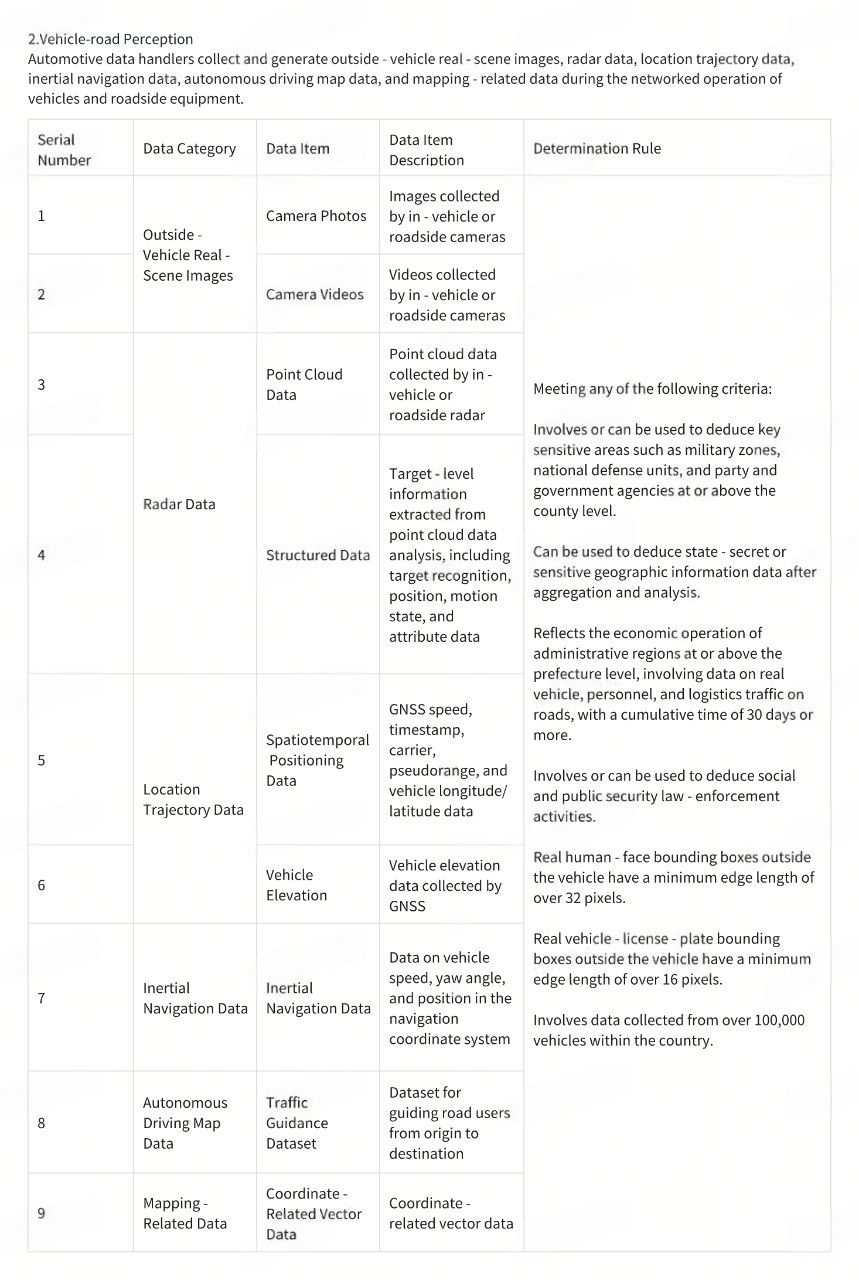
(1) R&D Design Scenario
(4) Software Upgrade Service Scenario
Automotive data handlers upgrade the source code of software packages corresponding to the powertrain system, chassis system, and safety - driving functions.
(5) Networked Operation Scenario
(6) Other Situations
Motor vehicle data meeting either of the following scenarios:
Motor vehicle data in other outbound business scenarios meeting the above determination rules.
Automotive data handlers identify and report important data in line with national regulations and industry standards. The Ministry of Industry and Information Technology, the Cyberspace Administration of China, and other relevant departments publicly announce or inform enterprises that such data is classified as important data.
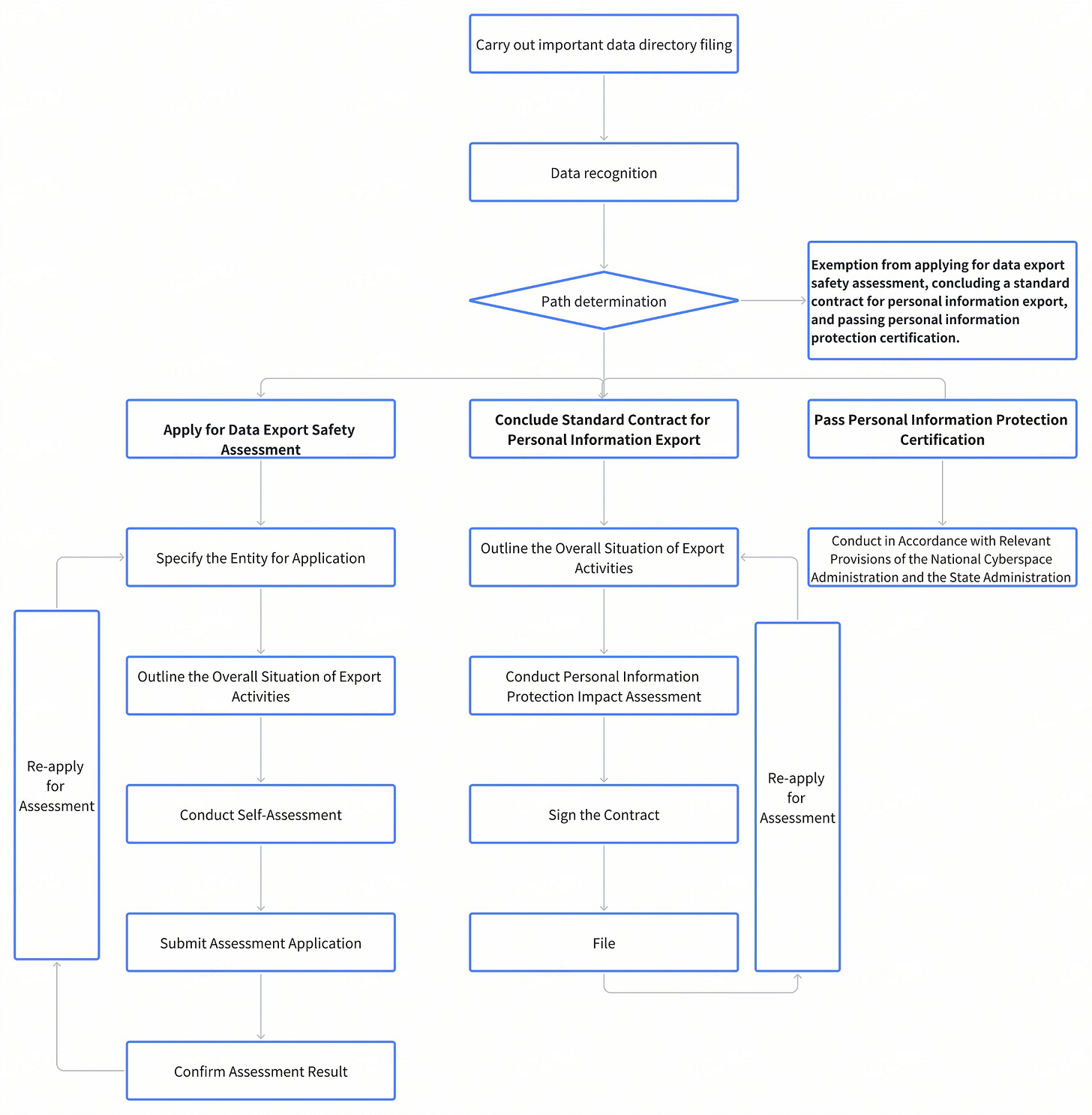
Chapter Ⅲ: Data Outbound Implementation Process
The data outbound implementation process is illustrated in the following chart:
(1) Data Identification
Automotive data handlers identify automotive data requiring declaration for export security assessment, conclusion of standard contracts for personal information export, and passing personal information protection certification, based on the filing of important data catalogs and in accordance with these Guidelines.
For the provision of personal information to overseas recipients, automotive data handlers shall fulfill obligations such as notification, obtaining separate personal consent, and conducting personal information protection impact assessments, in accordance with laws and regulations.
(2) Path Determination
Determine and confirm the data export path in line with the "Chapter I, General Provisions, (3) Data Export Path" of these Guidelines. If the circumstances specified in Item 3 of "Chapter I, General Provisions, (3) Data Export Path" of these Guidelines are met, the declaration for data export security assessment, conclusion of standard contracts for personal information export, and personal information protection certification are exempted.
(3) Implementation of Data Export Security Assessment
Automotive data handlers shall conduct data export security assessments in accordance with the "Measures for Data Export Security Assessment," the "Regulations on Promoting and Regulating Cross-border Data Flows," and the "Guidelines for Declaration of Data Export Security Assessment (Second Edition)."
Identification of the Declaration Entity
Automotive data handlers should submit applications for data export security assessment through a legal entity within China. If no legal entity exists within China, the domestic branch shall submit the application. If multiple domestic subsidiaries belong to the same parent company and have similar data export scenarios, the parent company may act as the declaration entity and submit a consolidated application.
Outline the Overall Situation of Export Activities
Collect materials from the enterprise and relevant overseas recipients, and outline the overall situation of export activities, including the following:
a) Basic information of the automotive data handler, including equity structure, actual controller, domestic and overseas investment status, etc.
b) Situation of the data proposed for export by the automotive data handler, including:
i. Business and data assets involved in the data export scenario.
ii. Purpose, scope, and method of data export.
iii. Details of the data items to be exported, presented in a list format.
iv. Domestic storage systems, data centers (including cloud services), data export channels, and planned overseas storage facilities for the data to be exported.
v. Situations regarding the provision of exported data to other overseas recipients.
vi. Statistics on the number of personal information exports in the current year (deduplicated) and estimated exports for the next three years.
c) The automotive data handler's data security保障 capability, including data security management, technical capabilities, proof of the effectiveness of data security measures, and compliance with relevant laws and regulations on data and network security.
d) Information on the overseas recipient, including its basic details, purposes and methods of data processing, and management and technical measures and capabilities for fulfilling responsibilities and obligations.
e) Legal agreements with the overseas recipient on the exported data, clarifying responsibilities and obligations. Specific content includes:
i. Purposes, methods, and scope of data export, and the overseas recipient's purposes and methods of data processing.
ii. Overseas storage location, duration, and measures for handling exported data upon expiration, completion of agreed purposes, or termination of the legal agreement.
iii. Restrictions on the overseas recipient's retransfer of exported data to other organizations or individuals.
iv. Safety measures the overseas recipient must take in cases of substantial changes in actual control or business scope, changes in data protection policies or the cybersecurity environment of the recipient's country or region, or other force majeure events.
v. Remedial measures, breach responsibilities, and dispute resolution for violations of data protection obligations.
vi. Requirements for emergency response and safeguarding individuals' rights in cases of data tampering, damage, leakage, loss, transfer, or illegal acquisition or use.
f) Other situations the automotive data handler deems necessary to explain.
Conduct Self-Assessment
a) Self-Assessment Matters
Automotive data handlers should focus on assessing the following matters in combination with the overall situation of data export activities and relevant materials:
i. Legality, legitimacy, and necessity of the purposes, scope, and methods of data export and the overseas recipient's data processing.
ii. Scale, scope, type, and sensitivity of the exported data, and potential risks to national security, public interest, and the legitimate rights of individuals or organizations.
iii. The overseas recipient's ability to ensure the security of exported data through its committed responsibilities and management and technical measures.
iv. Risks of data tampering, damage, leakage, loss, transfer, or illegal acquisition or use during and after export, and the availability of channels for safeguarding personal information rights.
v. Whether the proposed contract or legally binding document with the overseas recipient adequately addresses data security responsibilities.
vi. Other matters that may affect the security of data export.
b) Identify Issues and Rectify
If risks and issues affecting data export are identified during the self-assessment, automotive data handlers should promptly rectify them and document the related situations.
c) Formulate Self-Assessment Conclusion
Based on the risk self-assessment and rectification efforts, automotive data handlers should provide an objective self-assessment conclusion for the proposed data export activities and fully explain the reasoning.
d) Prepare Self-Assessment Report
Automotive data handlers should compile a data export risk self-assessment report, including the self-assessment process, overall export situation, risk assessment, and conclusion, along with relevant supporting documents.
Assessment Declaration
a) Prepare Declaration Materials
Automotive data handlers should prepare declaration materials in accordance with relevant regulations, including:
i. Copy of the Unified Social Credit Code certificate.
ii. Copy of the legal representative's ID document.
iii. Copy of the handler's ID document.
iv. Power of attorney for the handler.
v. Data export security assessment application form.
vi. Proposed contract or other legally binding documents with the overseas recipient.
vii. Data export risk self-assessment report.
viii. Other relevant supporting documents.
ix. The automotive data handler is responsible for the authenticity of the submitted materials. Submission of false materials will result in assessment failure and legal liability.
b) Determine Declaration Method
Generally, online declaration applies to automotive data handlers other than critical information infrastructure operators. Offline declaration is used for critical information infrastructure operators or other cases unsuitable for online declaration.
c) Submit Assessment Materials
Automotive data handlers should submit materials to the cyberspace administration department for data export security assessment in accordance with national regulations and modify or supplement materials as required.
Confirmation of Assessment Results
Automotive data handlers should conduct data export activities in compliance with relevant laws and regulations and the requirements of the assessment result notification. If there are objections to the assessment results, a re-evaluation may be requested within 15 working days of receiving the notification.
Reapplication for Assessment
Under any of the following circumstances, automotive data handlers should reapply for a data export security assessment:
a) Changes in the purpose, method, scope, or type of data provided overseas or in the overseas recipient's data processing purposes or methods, which affect the security of exported data.
b) Extension of the overseas storage period for personal information and important data.
c) Changes in the data protection policies, cybersecurity environment of the overseas recipient's country or region, or other force majeure events.
d) Changes in the actual control of the automotive data handler or the overseas recipient.
e) Changes in the legal agreement between the automotive data handler and the overseas recipient affecting data export security.
f) Upon expiration of the assessment result's validity period, if data export activities need to continue but the conditions for extending the assessment results are not met.
g) If data export activities that have passed the assessment are terminated due to non-compliance with data export security management requirements during actual processing, and the automotive data handler needs to continue data export activities after rectification in accordance with relevant requirements.
h) Other circumstances affecting the security of data export.
(4) Conclusion of Standard Contracts for Personal Information Export
Automotive data handlers should conclude standard contracts for personal information export in accordance with the "Measures for the Standard Contract on Personal Information Export" and the "Guidelines for Filing of Standard Contracts for Personal Information Export (Second Edition)."
Outline the Overall Situation of Export Activities
Collect materials from the enterprise and relevant overseas recipients to outline the overall situation of export activities, including the following:
a) Basic information of the automotive data handler, including equity structure, actual controller, domestic and overseas investment status, organizational structure, personal information protection body information, overall business operations, and personal information processing activities.
b) Details of the proposed personal information export, including:
i. Business activities, collection and use of personal information, and information systems involved in the personal information export.
ii. Purposes, scope, and methods of personal information processing by the automotive data handler and the overseas recipient.
iii. Scale, scope, type, and sensitivity of the personal information to be exported, including processing of sensitive personal information.
iv. Domestic storage systems, data centers, and other facilities for the personal information to be exported, related data export channels, and planned overseas storage facilities.
v. Situations regarding the provision of exported personal information to other overseas recipients.
c) Information on the overseas recipient, including its basic details, purposes and methods of personal information processing, and management and technical measures and capabilities for fulfilling responsibilities and obligations.
d) Other situations the automotive data handler deems necessary to explain.
Conduct Personal Information Protection Impact Assessment
a) Assessment Matters
In combination with the overall situation of personal information export activities and relevant materials, automotive data handlers should focus on assessing the following:
i. Legality, legitimacy, and necessity of the purposes, scope, and methods of personal information export and the overseas recipient's personal information processing.
ii. Scale, scope, type, and sensitivity of the exported personal information, and potential risks to national security, public interest, and the legitimate rights of individuals or organizations.
iii. The overseas recipient's ability to ensure the security of exported personal information through its committed obligations and management and technical measures.
iv. Risks of personal information tampering, damage, leakage, loss, or illegal use after export, and the availability of channels for safeguarding personal information rights.
v. Impact of the overseas recipient's country or region's personal information protection policies and regulations on the implementation of the standard contract.
vi. Other matters that may affect the security of personal information export.
b) Identify Issues and Rectify
If risks and issues affecting personal information export are identified during the assessment, automotive data handlers should promptly rectify them and document the related situations.
c) Formulate Personal Information Protection Impact Assessment Conclusion
Based on the personal information protection impact assessment and rectification efforts, automotive data handlers should provide an objective assessment conclusion for the personal information export activities and fully explain the reasoning.
d) Prepare Personal Information Protection Impact Assessment Report
Automotive data handlers should compile a personal information protection impact assessment report, including the assessment process, overall export situation, risk assessment, and conclusion.
Contract Signing
Automotive data handlers should sign a standard contract for personal information export with the overseas recipient.
Filing
a) Material Submission
Automotive data handlers should submit filing materials to the cyberspace administration department in accordance with national regulations. These materials include copies of the Unified Social Credit Code certificate, the legal representative's ID document, the handler's ID document, a power of attorney, a commitment letter, the "Standard Contract for Personal Information Export," and the "Personal Information Protection Impact Assessment Report." They should also submit supplementary materials as required.
b) Result Feedback
After obtaining the filing number, automotive data handlers should conduct personal information export activities in compliance with relevant laws and regulations on personal information export security management.
Supplementary or Refiling
During the validity period of the standard contract, if any of the following circumstances occur, automotive data handlers should conduct a new personal information protection impact assessment, supplement or conclude a new standard contract, and fulfill the corresponding filing procedures:
a) Changes in the purpose, scope, type, sensitivity, method, or storage location of personal information provided overseas, or changes in the overseas recipient's purposes or methods of personal information processing.
b) Extension of the overseas storage period for personal information.
c) Changes in the overseas recipient's country or region's personal information protection policies or regulations that may affect personal information rights.
d) Other circumstances that may affect personal information rights.
(5) Personal Information Protection Certification
This is conducted in accordance with relevant regulations from the National Cyberspace Administration, the State Administration for Market Regulation, and other departments.
Chapter IV:Safety Protection Requirements for Automotive Data Export
(1) Management Requirements
Department Requirements
Automotive data handlers should establish a dedicated department for automotive data export within the enterprise to coordinate data export security management and oversee the implementation of relevant management requirements.
Personnel Requirements
Automotive data handlers should appoint a data export security officer to oversee data export activities and the effectiveness of protective measures, ensuring the security of data export activities.
System Requirements
Automotive data handlers should establish systems for cybersecurity, data security, and personal information protection, with specific requirements for automotive data export security management.
Approval Requirements
Automotive data handlers should set up an internal registration and approval mechanism for automotive data export, defining approval authorities and processes, and maintaining records of approval materials.
(2) Protective Technology Requirements
Data Export Transmission Security
Automotive data handlers should implement the following protective measures:
a) Ensure the confidentiality and integrity of automotive data during export transmission using validation technologies, cryptographic technologies, secure transmission channels, or secure transmission protocols.
b) Systems related to automotive data export should have the capability to authenticate the identity of overseas data recipients to ensure their authenticity.
Data Export Security Monitoring Requirements
Automotive data handlers should monitor automotive data export transmission behaviors, log security events, and retain the logs.
Inspection Support Requirements
Systems related to automotive data export should provide technical support for data export security inspections, retain raw data export traffic, and support data anti-tampering and content parsing.
a) Full Retention. Retain all data export traffic for one week based on start and end times.
b) Sampling Retention. Support sampling retention of data export traffic based on start and end times or IP address ranges, with a retention period of at least one month.
(3) Log Requirements
Log Recording
a) Network Traffic Logs
Automotive data handlers should record automotive data export communication behaviors, including dates, times, source and destination IP addresses and ports, transport layer protocol, application layer protocol, and packet sizes, forming and retaining communication logs.
b) Operational Behavior Logs
Automotive data handlers should record operational behaviors on hosts directly transmitting automotive data overseas, including user information, operation time and objects, operation types, login IPs, and device information, forming and retaining operational behavior logs.
Log Retention
Automotive data handlers should retain network traffic logs, operational behavior logs, and security logs in tamper - proof formats for at least three years.
Log Auditing
Automotive data handlers should audit network traffic logs, operational behavior logs, and security logs, responding promptly to security risks such as illegal operations.
(4) Emergency Response Requirements
Automotive data handlers should establish capabilities for addressing unauthorized automotive data exports. Upon detecting abnormal behaviors, they should take timely measures and report to local industry regulators as required.